In today’s digital landscape, endpoints laptops, desktops, and mobile devices are prime targets for cyberattacks. A single compromised device can open the door to data breaches, ransomware, and identity theft. Endpoint & Mobile Security (EMS) ensures that every device accessing your network is secure, compliant, and resilient against threats.
A single compromised device can lead to data breaches, ransomware infections, and identity theft. That’s why Endpoint & Mobile Security (EMS) is critical for every business.
Why EMS Matters
Endpoints are the frontline of your organization’s cybersecurity. Without proper safeguards:
- Malware can infiltrate through unprotected devices.
- Sensitive data can be stolen via unauthorized apps or removable media.
- Botnets can exploit vulnerable systems for large-scale attacks.
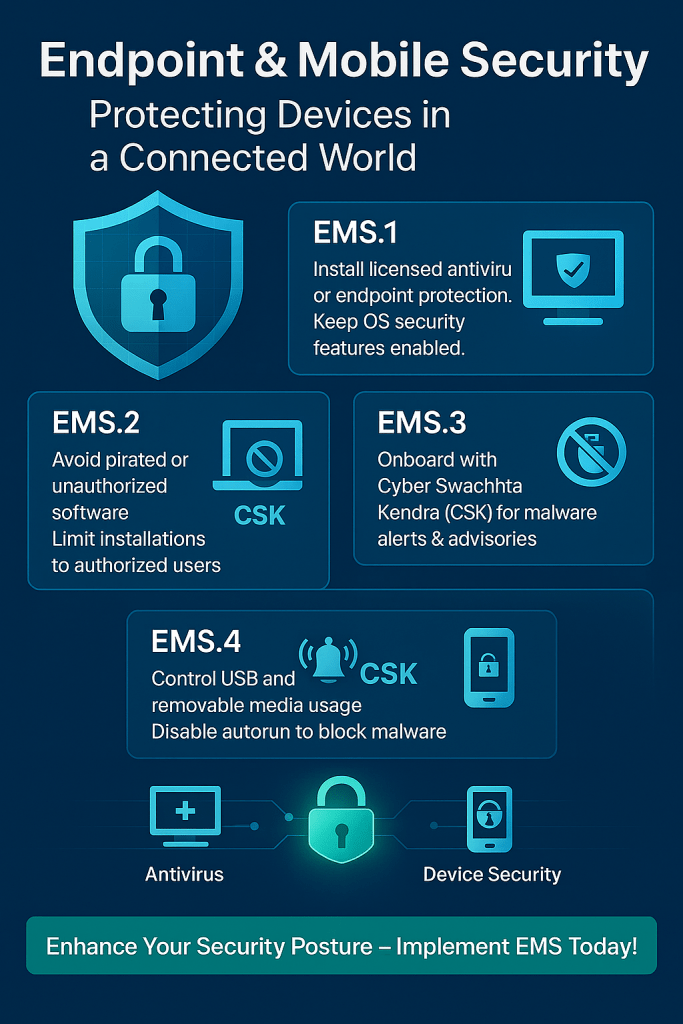
FinSequr’s EMS Best Practices
EMS.1: Install Licensed Endpoint Protection
- Deploy antivirus or endpoint protection software on all devices.
- Use licensed versions for vendor support and regular updates.
- Never disable built-in OS security features like Windows Defender or Windows Firewall.
EMS.2: Avoid Unauthorized Software
- Pirated software is a legal risk and a security nightmare.
- Restrict software installation to authorized personnel only.
- Maintain an approved software list for compliance.
EMS.3: Leverage CERT-In’s Cyber Swachhta Kendra
- Onboard with Cyber Swachhta Kendra (CSK) for:
- Botnet cleaning tools
- Malware alerts and advisories
- Stay informed about emerging threats and remediation steps.
EMS.4: Control USB & Removable Media
- Restrict or monitor USB usage.
- Disable autorun features to prevent malware spread.
- Consider endpoint management tools for granular control.
Real-World Example
In 2023, a major Indian NBFC faced a ransomware attack after employees installed unauthorized software on their laptops. The malware spread through USB drives, encrypting sensitive financial data.
Impact: Operations halted for 72 hours, causing financial losses and reputational damage.
Lesson: Strict endpoint security policies and USB control could have prevented this breach.
Compliance Requirements
- ISO 27001: Requires documented endpoint security processes.
- CERT-In Guidelines: Mandate malware protection and monitoring.
- RBI Cybersecurity Framework: Enforces strict controls for financial institutions.
FAQ
Q1: Why is endpoint security critical for remote work?
A: Remote devices often connect to unsecured networks, increasing risk.
Q2: Can mobile devices be as vulnerable as desktops?
A: Yes, mobile malware and phishing attacks are rising rapidly.
Resources
FinSequr Insight
Endpoints are the gateway to your organization’s data. By enforcing EMS policies, you reduce risk, improve compliance, and build a resilient security posture. Remember: every device matters in the fight against cyber threats.
Visit FinSequr.com for more cybersecurity insights or contact our experts today.

Leave a comment