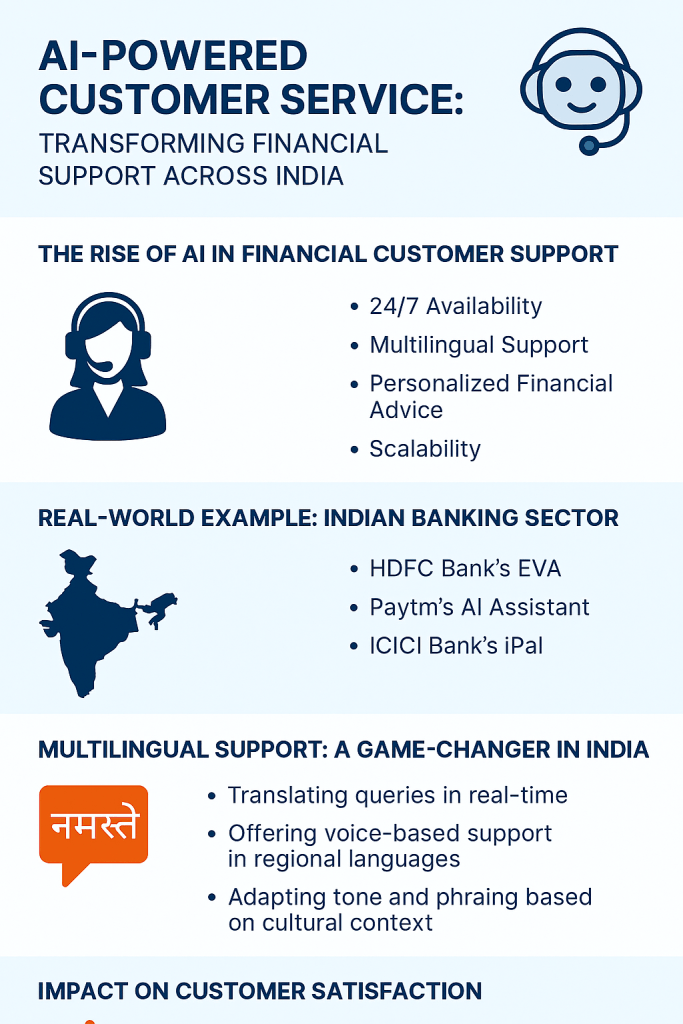
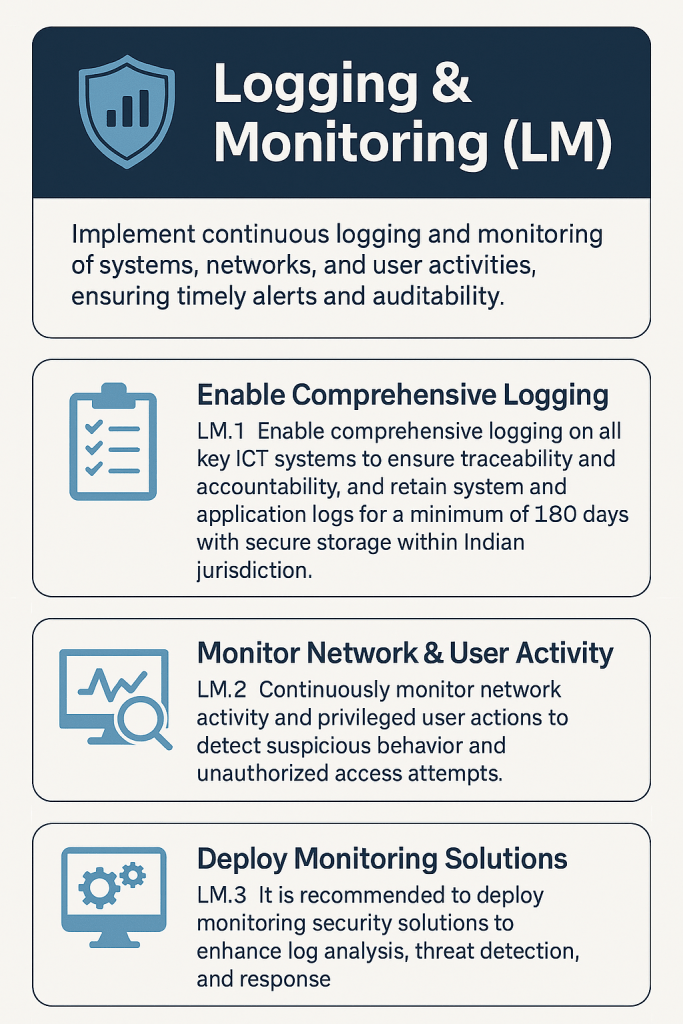
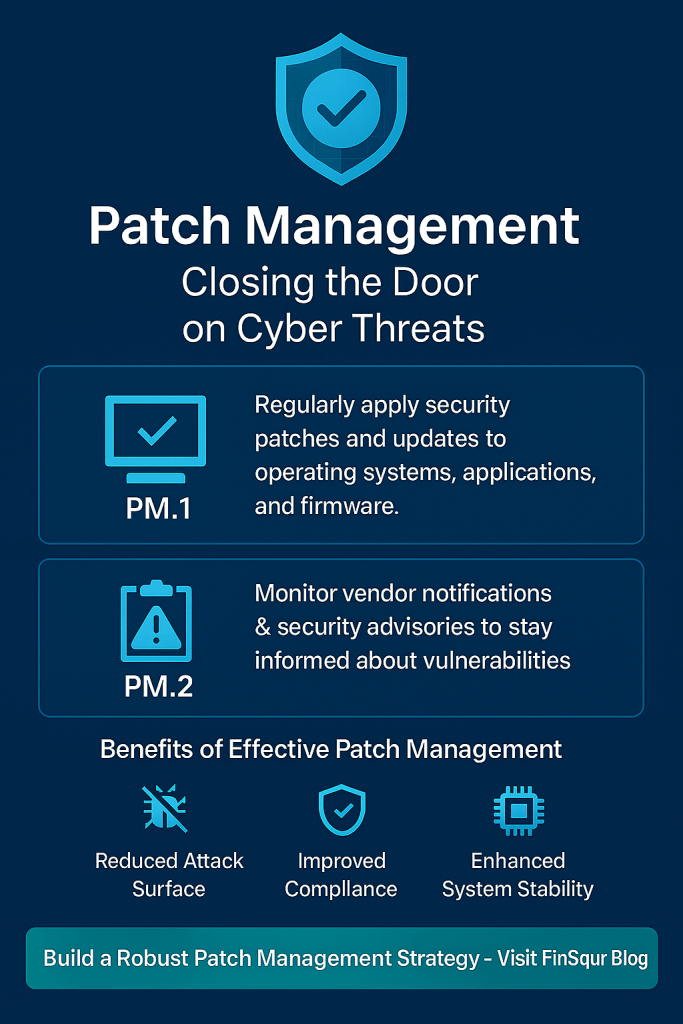
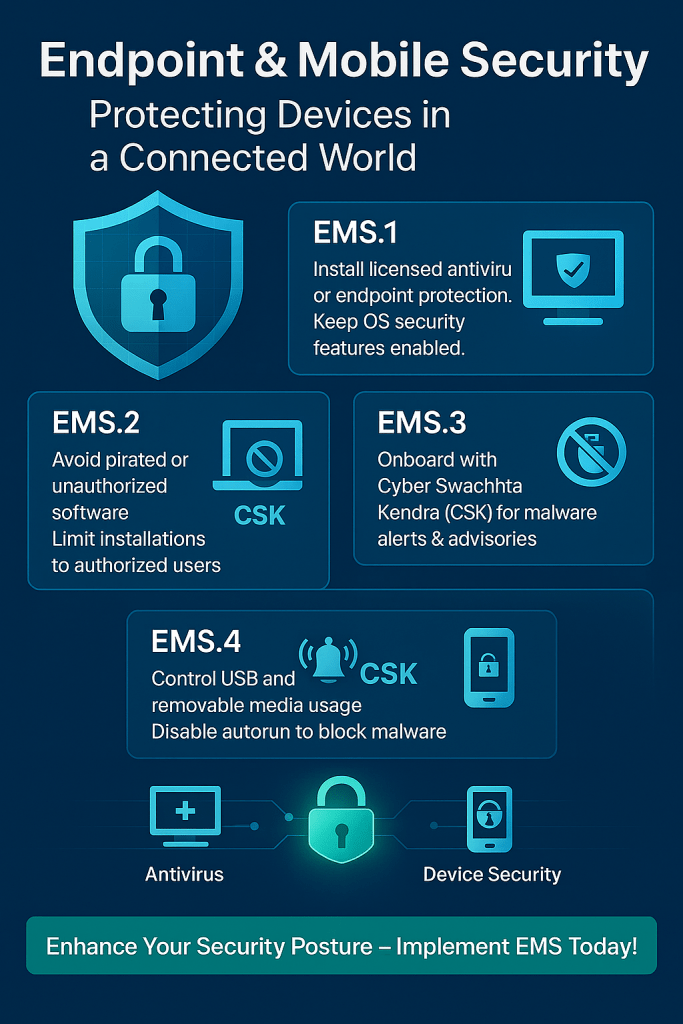
The Digital Personal Data Protection Act (DPDPA), 2023 is India’s landmark legislation aimed at safeguarding personal data in the digital age. With increasing cyber threats and data misuse, this Act ensures that individuals have control over their personal information while businesses follow strict compliance norms.
Why Was This Act Introduced?
India is one of the fastest-growing digital economies, with millions of users sharing personal data online every day. From banking apps to e-commerce platforms, data is everywhere.
The DPDPA was introduced to:
- Protect individuals’ privacy.
- Prevent misuse of personal data.
- Establish accountability for organizations handling data.
Key Features of the Act
1. Consent-Based Data Processing
Organizations must obtain clear consent before collecting or processing personal data.
2. Rights of Individuals (Data Principals)
• Right to access information about how your data is used.
• Right to correct or delete your data.
• Right to withdraw consent anytime.
3. Obligations for Businesses (Data Fiduciaries)
• Implement reasonable security safeguards.
• Report data breaches promptly.
• Appoint a Data Protection Officer for compliance.
4. Penalties for Non-Compliance
Fines can go up to ₹250 crore for serious violations.
Impact on Financial Sector
Banks, NBFCs, and fintech companies handle sensitive data like Aadhaar, PAN, and transaction details. Under DPDPA:
- Customer consent becomes mandatory for every data use.
- Data minimization: Collect only what is necessary.
- Strong encryption and breach reporting are essential.
Example:
If a bank uses customer data for marketing without consent, it can face heavy penalties under the Act.
How Can Businesses Prepare?
- Conduct Data Protection Impact Assessments.
- Train employees on privacy compliance.
- Update IT systems for secure storage and transfer.
What Does It Mean for You as a Consumer?
- You have the right to know how your data is used.
- You can request deletion of your data from any platform.
- You can report misuse to the Data Protection Board.
Final Thoughts
The DPDPA is a big step toward making India’s digital ecosystem safer and more transparent. For businesses, compliance is not optional hence it’s a necessity. For individuals, it’s a win for privacy and security.